The Challenge
Frameworks like SOC 2, ISO 27001, and PCI DSS expect ongoing proof of control effectiveness, not a PDF you assemble once a year. Manual compliance processes drain resources and leave gaps that auditors will find.
Common Pain Points & How ZeroPath Solves Them
| Pain Point | How ZeroPath Solves It |
|---|---|
| Last-minute audit scrambles Teams rush to gather evidence weeks before audits | Continuous compliance tracking Every scan generates fresh audit evidence automatically |
| Manual evidence collection Hours spent compiling spreadsheets and screenshots | Automated evidence packs Schedule weekly exports to Vanta, Drata, or ServiceNow GRC |
| Control mapping confusion Unclear which findings map to which controls | Control-aligned scanning Each finding mapped to exact control clauses |
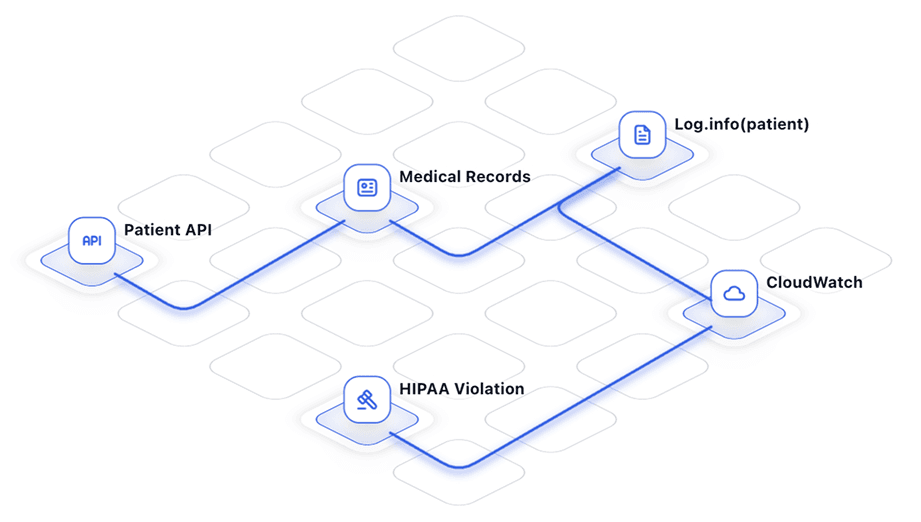
| Data privacy compliance PHI/PII leaks go undetected in code | Natural language detection Custom rules deployed in minutes across your organization |
How it Works
1. Scan
SAST, SCA, secret, and IaC scans map each finding to exact control clauses
2. Track
Dashboards show MTTR, SLA breaches, and risk trends by business unit
3. Report
Schedule evidence packs with signed SBOMs and fix verification records
4. Attest
Generate audit-ready attestations with cryptographic proof of compliance
Key Capabilities
Control-Aligned Scanning
- SOC 2 mapping - Direct alignment to all relevant Trust Service Criteria
- ISO 27001 coverage - Automated evidence for Annex A controls
- PCI DSS requirements - Continuous monitoring of Requirements 6.x
- Custom frameworks - Map to your organization's specific controls
Automated Evidence Collection
- Signed SBOMs - Complete dependency tracking with cryptographic signatures
- Immutable scan logs - Tamper-proof records with timestamps
- Fix verification - Automated proof of remediation timelines
- Policy compliance - Evidence of security policy enforcement
Enterprise Organization
- Workspace isolation - Separate environments for subsidiaries or client projects
- Granular RBAC - Enforce least-privilege access across teams
- Multi-tenant architecture - Secure data segregation for different business units
- Audit trails - Complete activity logs for compliance reviews
Data Privacy Protection
- PHI/PII detection - Natural language rules find sensitive data patterns
- GDPR compliance - Detect personal data processing in code
- Custom rule creation - Deploy organization-specific rules in minutes
- Cross-repository enforcement - Consistent privacy protection everywhere