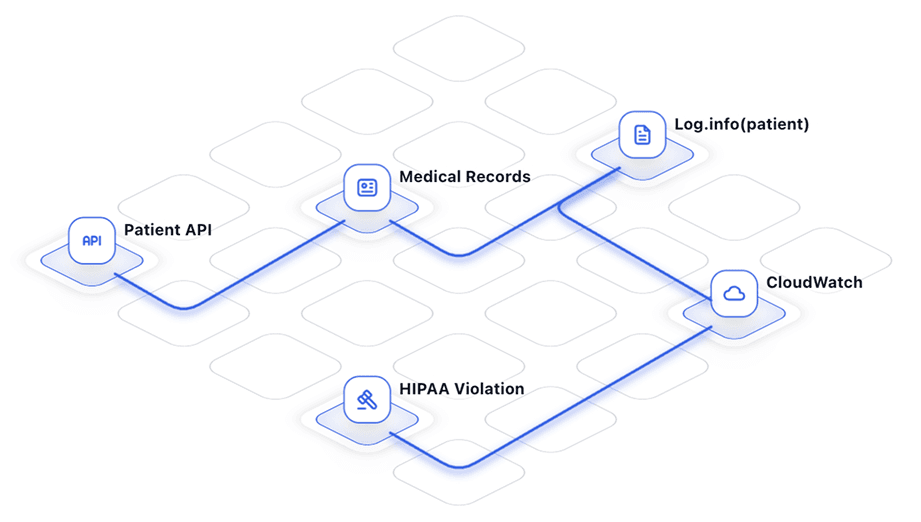
The Challenge
Picture a typical sprint: a PR lands ten minutes before cut-off. Your scanner flags 3 items, two of them false. The team rolls the dice and deploys. Six months later Incident Response is on the call.
ZeroPath rewrites that story: an on-push scan runs in under 60 seconds, returns only three exploitable issues, and supplies ready-to-merge patches that match your code style.
Common Pain Points & How ZeroPath Solves Them
| Pain Point | How ZeroPath Solves It |
|---|---|
| Legacy scanners flood developers with noise Teams ignore security alerts due to false positive fatigue | 92% alert reduction AI-powered analysis shows only real, exploitable vulnerabilities |
| Security fixes break functionality Generic patches don't understand your codebase | Context-aware autopatch Generates fixes that match your code style and preserve functionality |
| Vulnerabilities discovered too late Finding issues in production is expensive and risky | Shift-left security Sub-minute scans catch issues at commit time, not deployment |
| Developers lack security expertise Not everyone knows how to fix complex vulnerabilities | Built-in security guidance Clear explanations and one-click fixes empower every developer |
How it Works
1. Scan
Real context SAST detects SQLi, XSS, SSRF, broken authN/authZ, and business logic issues
2. Prioritize
AI scores issues based on CVSS 4.0, considering entire context to prevent wasted developer time
3. Fix
Autopatch generates a secure diff in your branch that matches your coding standards
4. Verify
Fail-safe CI blocks until vulnerability is verified as fixed (with audited break-glass option)
Key Capabilities
Comprehensive Security Coverage
- Real context SAST - Ability to detect SQLi, XSS, SSRF, broken authN/authZ, and business logic issues
- Credential guard - Detects hard-coded keys and leaked tokens the moment they appear
- Dependency analysis - Identifies vulnerable libraries and suggests secure alternatives
- Infrastructure as Code - Secures Terraform, CloudFormation, and Kubernetes configurations
Developer Experience
- Pull request automation - Security reviews happen automatically on every PR
- Clear remediation guidance - Understand why something is vulnerable and how to fix it
- Learning mode - Improves accuracy based on your team's feedback
- Less noise - 80% lower false positive rate than traditional alternatives
Enterprise Features
- Custom policy enforcement - Implement your organization's specific security requirements
- Compliance reporting - Track SOC2, PCI-DSS, and other compliance requirements
- Security metrics dashboard - Measure and improve your security posture over time
- Role-based access control - Control who can view and override security findings