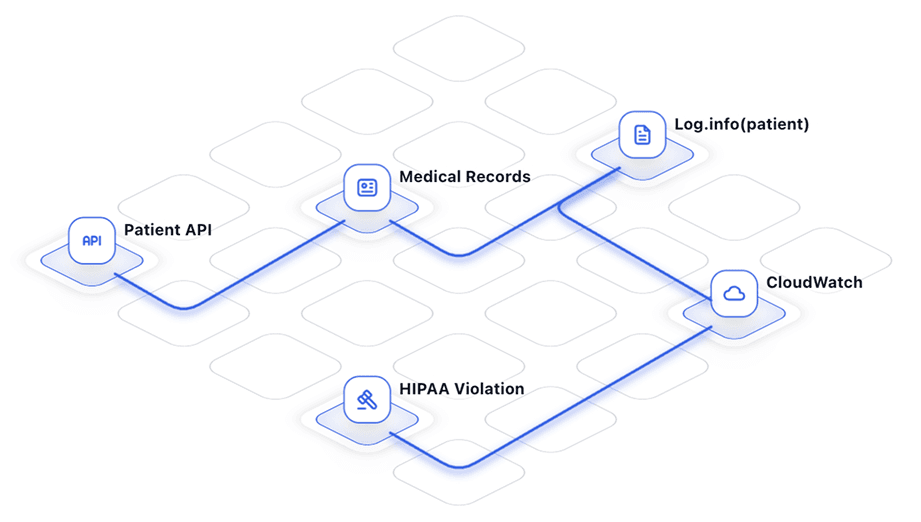
The Challenge
APIs can change with every deployment, and all of it has to remain indexed. Adopting specific frameworks can help impose structure, but what about legacy code or shadow endpoints that eschew those policies? In a large organization with diverse applications, keeping a good overview of your current API posture often means either imposing bureaucratic structure on your developers or requiring security engineers to sift through documentation and code on their own time.
Common Pain Points & How ZeroPath Solves Them
| Pain Point | How ZeroPath Solves It |
|---|---|
| No single system for organizing and registering endpoints | LLMs crawl your codebase for input handlers |
| Static SASTs have no visibility or understanding of auth | Universal business logic and authentication scanning |
| Static scanners see code but ignore live request paths | Source-to-sink analysis links route definitions to handler logic |
| Security teams sift through piles of false positives | Reachability checks hide unreachable endpoints and unused functions |
How it Works
1. Discover
Automatically map all API endpoints across REST, GraphQL, gRPC, and WebSockets
2. Analyze
Trace data flows from endpoint to database, understanding authentication and authorization
3. Detect
Identify OWASP API Top 10 vulnerabilities and business logic flaws
4. Protect
Generate fixes and update API documentation automatically
Key Capabilities
API-Focused Features
- Automatic discovery of REST, GraphQL, gRPC, and WebSocket routes
- Data-flow tracing that surfaces broken auth, business logic flaws, injection issues, and SSRF
- Secret detection for leaked tokens and keys used in API calls
- Instant Swagger and OpenAPI spec export to keep docs in sync with reality
Advanced Security Detection
- Broken Object Level Authorization (BOLA) - Detect when users can access resources they shouldn't
- Broken Function Level Authorization - Find admin endpoints exposed to regular users
- Mass Assignment vulnerabilities - Identify when APIs accept unexpected parameters
- Rate limiting analysis - Ensure proper throttling on sensitive endpoints
- Input validation gaps - Catch missing sanitization before data hits your database
Developer-Friendly Integration
- Pull request comments - Security feedback appears directly where developers work
- API security scorecard - Track security posture improvement over time
- Postman collection generation - Export secure API test suites
- CI/CD pipeline integration - Block deployments with critical API vulnerabilities